A vulnerability in the Log4j-core Java library was found in early December 2021, which allows hackers to potentially access servers remotely and execute arbitrary code, in other words: taking control of a server. Within the Java environment, the Log4j software module is extensively used, as it’s one of many building blocks that are used in many organizations to create software nowadays.
It’s a race against time to have everything under control; update your software, check for new vulnerabilities in your organisation….
How to prevent and what to do?
Check the list of vulnerable software and update to the latest version of Log4j. Contact your software vendors. Vendors like CTModule, which fortunately, can confirm that we are not affected by this vulnerability. Additionally, we suggest to following the advice of Apache, which recommends updating to 2.17.1 immediately. You can find the latest Log4j apache security updates at: https://logging.apache.org/log4j/2.x/security.html
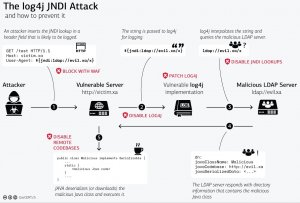
Source: GovCERT.ch
What next?
We know that simply updating Log4j may not resolve issues if your company is already compromised. Therefore, we recommend to continuously investigating activity in your environment, and act in accordance to reduce exposure. Experience tells us not to let our guard down, this is why CTModule will continue to actively monitor the situation and inform our partners about any possible evidence in our systems.
This is again a clear wake-up call for regulatory institutions and organizations to stay tuned and keep the security level on the highest priority.